Todd M. Bezenek
As the Dakota/Lakota Sioux Indigenous Tribes say, "Hau."I'm a three-time fellow: NSF (NASA), NSF (MaCE--mathematics and computation in engineering), and UWCS first year outstanding graduate researcher in computer architecture. I've worked in cache memories, networking, database systems for high-throughput cloud storage, performance of stand-alone and web applications, and hardware/software co-design for network security.
Who invented the number zero?
If you want to contact me, please use my LinkedIn to find me. If you have no other way, feel free to call me, but only if you cannot get me via LinkedIn. The number is plus one, sicks five zero - five one too - nine one one fore.
Here are slides for my talk Is This S*IT Safe?! at the inagural Silican Valley Artificial Intelligence Meetup. The password for the slides is "xyzzy".
The Meetup was originally scheduled to take place in person at Stanford, but a large signup moved it to the Web. I was honored to speak for 30 minutes before Boris Ivanovic, the Director of Autonomous Driving Research at nVIDIA. The most interesting part Boris's talk was the demonstration of Shannon's Theorem in the behavior seen when the training data collection times do not match up with the inference times.
I have, since the talk, seen a slide showing the same phenomenon presented by the IBM watsonx team. Their graph was right up there with the "Napolean March" graph. Nice work, IBM. You discovered the same thing nVIDIA did. You are getting slow in your old age.
My Emblem/Logo/Cause (at the top-right corner of this page)
(Please click on the emblem to visit the Unicode Consortium Website.)
I sponsor the Unicode equals sign1 as a representation of all people which are and should be considered equal. Please treat your fellow humans the way you wish to be treated in return.Given the opportunity to live where rights are earned or where rights are purchased, I prefer to live where they are earned, which means I must and try to live up to the equals sign, rather than only support it financially.
Donation of Cloud Computing Resources
I am encouraging cloud computing providers to donate their unused Cloud Compute Credits to charity. I recommend donating to the Network Contagion Research Institute (NCRI) which works to reduce deception, manipulation, and hate on the Internet.Another option is the Stanford Internet Observatory (SIO), part of the Stanford Cyber Policy Center, which works to build the necessary tools—access to data, information processing resources, and talent—to study the negative impact of emerging information technologies and how they can be abused or used to abuse individuals or groups.
Of particular interst moving forward will be SOI's open Journal of Online Trust and Safety.
What I'm Working on Right Now (June, 20, 2023)
Note: (tm verified) means they belong to Todd Bezenek and/or Mari Sailer, are the most broad trademark possible, and they cover commerce in the least-expensive-thing-to-produce-ever after things that are 100% free: computer software.Hybrid Human/Computer systems, using Root Technology(tm verified), and Perceptive Security(tm verified). The name of my company is Omnifidus(tm verified).
The Omnifidus trademark is in the area of Software design. The other two are in the area of Copying of computer software.
All three are in International Class 042. Yes, 42. The answer to life, the universe, and everything. Also known as ASCII character "*".
Perceptive Security Is:
DARPA defines four pilliars of security: physical, logical, cryptographic, and temoporal. But, where does camoflauge fit? Most people say "physical". Where does fake news fit? Most people say logical. If you add a new pillar, cognitive security, everything fits.However, if you instead use the term perceptive security, the pillar is much stronger.
Root Technology Is:
The idea behind root technology is to use man-made/invented technology which is simple, proven, well-understood, and just plain works. Examples include: hammer, knife, and wheel. For interest, natural, non-man-made technolgies include: fire, water, air, electric current, gravity, light, etc. Where does mathematics fit? How about logic?Companies Using Root Technology (list is incomplete):
TelegramOmnifidus. Note: This company currenty belongs to me and my wife. It controls Root Technology and Perceptive Security. The company is actively engaged in commerce in computer software. Out first patent will be submitted when we have a description of the implemtation of the idea we are working on: Wisdom. I'll change the name if someone steals it. The implementation will be the source code used to implement the first prototype. It will be one of the most bulletproof patents ever submitted. I'll be submitting it to WIPO, not USPTO, because WIPO is more powerful.
Only a few key people have heard what my company is doing and I can trust them all except for one. That one is Sam Cassidy and you can identify the unique one in the world by looking at something I Tweeted. One of them whom I can trust is David Blumberg. His Venture Capital company only deals in B2B commerce. Mine deals in B2C commerce.
A Summary of My Employment History
This is a quick summary of my early career as companies are often interested in how senior people started in the industry.Studying Computer Architecture and the Discovery of Program Phase Behavior
I am blessed to have been the first person (that I know of--if you know of someone else, please let me know so I can fix this) to have recognized the signifiance of program phase behavior. This happend while writing and using the debugger developed to debug the Strata compiler in the late 1990s.Side note: Here is a meta-paper (link: https://courses.cs.washington.edu/courses/cse590g/03au/Comparing.pdf) about Program Phase Behavior which was later published by my PhD advisor and a great student in computer architecture who started working for Jim Smith after I got fired. (See a note about being fired from jobs below.)
Side note: The Strata compiler was the first Java-to-metal full implementation of Java bytecodes. Although there were three people on the team that developed the compiler, I would like to point out that Subramanya Sastry was the driving force which made the compiler possible.When I started at the University of Wisconsin, I was supported by a Mathematics and Computation in Engineering National Science Foundation fellowship. I quickly found that I did not want to study Computer Vision, but Computer Architecture.The compiler predated LLVM and included many of the same uses of type information. We were proud that the compiler was completed in approximately 13 months and a compiler team from IBM who visited us was flabbergasted that we were able to build an idempotent compiler from scratch in such a short time. They had to be reminded that as graduate students, we were able to by much more focused than those working in industry with families to nurture on the side.
Computer Vision to Recognize Which Plants to Squirt With Herbicide
I wrote my Master's Thesis (titled "Recognition of Juvenile Plants") on how to identify plant species using the technology I knew about at that time. When I later studies at the Wisconsin, I took a class in linear programming (LP) (we call it Machine Learning today) from Nike Street's PhD advisor (link: https://minds.wisconsin.edu/handle/1793/64580). I can't remember the professor's name right now, but he was the first one I met after I got to Wisconsin.In any case, the LP would have made my thesis project 100% accurate instead of only 98% accurate. I wish I had known about that when I was at NDSU, but it wasn't taught there.
Working with Mike Flynn at Stanford University
(later) Computer arithmetic. Chinese Government. MIPS. Cray. Hewlet-Packard Enterprises. IEEE Presidental Candidate.Working at MIPS and Esperanto (pick the right name from Wikipedia)
(later) Esperanto. MIPS Everywhere. Esperanto Might be the Next nVIDIA. MIPS is going to own Esperanto? Hmmm. It probaly already does.Why the RISC-V ISA is It
If I tell you that RISC-V is the future, I'm not telling you something you don't already know. If you don't know that, maybe you want to hire someone like me.Early Startups and StartDowns
During my career, I've been involved with three startups and one StartDown. All the startups were successful. Here is the story.The first StartDown: MIPS Technologies, Inc.
The Second and Third Startups
I quit only two jobs in my lifetime. They were the two jobs with startups I had simultaneously at the time I had to depart for Wisconsin from Fargo, ND. Those jobs were:
1. I was hired as engineer #2 at Metal Building Software. The company is still going strong 28 years after I left.
2. I was hired as one of a handful of engineers at Concord International, which had about 200 emoloyees at the time. I was hired to use some early artificial intelligence (AI) and fuzzy logic techniques to defeat selective availability on early global positioning system (GPS) (link: https://www.gps.gov/systems/gps/modernization/sa/). I was proud of the fact that, although I worked on the project for 13 months, the first day I suggested the solution the ended up using. If you are interested, just ask. The company was acquired by Case IH (link: https://www.caseih.com/en-us/unitedstates) shortly after I left.
The First Startup and a Missed Opportunity
I had the chance to work for someone who is now running to be President of the United States. Here is the story:I started working toward BS degrees in computer sciences and electrical and electronics engineering (theoretical basis of study) at the age of 15. I took some time off to work on the Pharmacy Statistical package running on a Digital Equipment Corporation (DEC) PDP-11.
I intervie
I have been fired from every job I've had except for two. The two I quit because I left Fargo, ND to work on a Ph.D. in computer vision at the University of Wisconsin.
If you are Interested in Hiring Me
I am currently working as a consultant at Intel in the Data Center (Cloud Infrastructure) Group. Since it is a consultant position of limited duration, I am interested in hearing about future opportunities. Please take a look at my LinkedIn profile or ask for a copy of my resume via email at bezenek(at)gmail.com if you are interested.I do SW/HW co-design in computer architecture and software systems. I interface with people who do RTL, but I do not do it myself other than small tweaks when needed. I'm the computer architecture and software expert who straddles the HW/SW line and knows as much as possible about the software side and how it interacts with the hardware architecture.
I also do software and systems performance tuning for scale, speed, and energy use.
Finally, I can do software development. I can work in embedded systems, large, scalable systems, and systems with workload-specific hardware. My background in both computer sciences and electrical engineering make me a versatile employee for building software systems.
Here are Some Highlights from My Work Experience:
- I did some of the ground-breaking work in the analysis of program phase behavior and its application to computer architecture, including processor design uses for improved performance while saving power at the same time.
- I enjoy the challenge of working in a cross-team setting. My broad background enhances my ability to contribute in that setting.
- I have an excellent experimental background and the ability to avoid faulty experiments and invalid conclusions. I have worked with several simulation technologies used to explore new architectural designs.
- I have worked with some of the best software/hardware/systems research people in the world, and I consider them my peers.
- I enjoy augmenting the abilities of those around me and vice-versa.
- Bonus: I have the ability to learn not only from marketing material, but from the technical research literature, so I learn the best solutions, not those most highly recommended by the people selling them.
Again, if you would like a copy of my resume, please send email to bezenek(at)gmail.com. I also read my email at bezenek(at)cs.wisc.edu, but not nearly as often.
Why I left Wisconsin Without a Ph.D.
I discovered something. The person who paid me to discover it wanted someone else to demonstrate its value, so I left for Intel Labs in Hilsboro, Oregon, USA. My boss there was Konrad Lai. His boss was Pat Gelsinger. They are both "A" people. I'm lucky that way.
My Research: Program Phase Behavior and Its Use to Impove Performance and Decrease Power Consumption
In 1998-99, my research focus was understanding program behavior and how knowledge of it can be applied in making architectural decisions. In particular, I studied workload phase behavior. One day I ate lunch with David Wood. He was interested in what I was doing, but pointed out I would have to show program phases existed before I could talk about them. I already had that.If you look at the work done by Brad Calder, et al., the figure at the bottom of his phase analysis website shows the phases in GCC. At the time I was studying phase behavior, the three most interesting benchmarks were GCC, Go, and Linux/Solaris/Windows NT.
I wish I saved one of my plots. I did not create graphs the way Calder et al. did. I created images which could be zoomed in on using Sun's image viewing software on Solaris. Using it, you could see one pixel on the screen as 10million instructions down to one pixel as 1,000 instructions. Now THAT's a 30,000ft view of a program.
This website has a color rendition of the content in the
2002 ISCA paper publised in IEEE Micro by invitation.
Introducing program phase behavior is not publishable on its own. An application
must be included. My application was configuring a reconfigurable bimode branch
predictor using the output of the Phase Detection and Prediction Unit, or
PDPU. The PDPU detects phases using a signature generated by the XOR of the last N
call targets stored in a ring buffer. Reproducability is guaranteed by XORin each
branch target when it enters the ring buffer and then XORing it again when the
target is removed as the head of the buffer comes back around. Andy Glew suggested
the XOR.
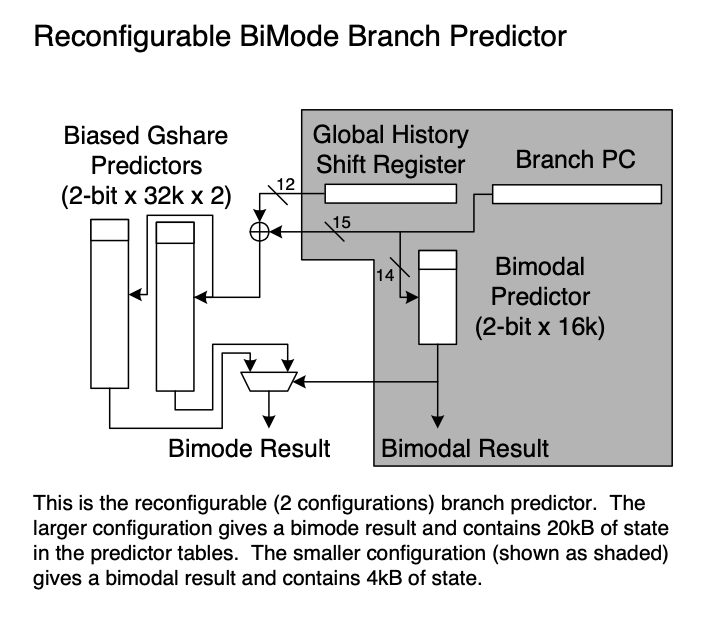
Looking at my 1999 diagram of the reconfigurable hybrid bimode predictor shown on the right, the choice of which of the two branch predictors to use is determined by the accuracy of the branch prediction results the last time the identified phase was executed. In this way, the bimodal predictor is used when we have highly predictable behavior for that prediction method, i.e., looping, and the bimode predictor is used when we do not.
The PDPU and reconfigurable predictor above are similar to what was published in a technical report at the University of Colorado in 2004.
When the bimodal predictor is being used, we turn off the bimode predictor. This saves power and eliminates destruction of the bimode predictor state by the part of the program which is easily predictable by the bimodal predictor. The resulting reconfigurable, hybrid predictor is both more accurate, i.e., performs better and uses less power than a standard bimode predictor.
I did not publish this work because my Ph.D. advisor was interested in pursuing something else, which did not get published because the paper was not written. My responsibility was building the experiemental infrastructure and gathering the results. The paper was being written by others and was not completed in a timely manner.
Please note all good ideas are going to be discovered if it is time. When I did not publish this work, Brad Calder and his students did the same thing because it was time for this to be done. My only disappointment is that something similar to the PDPU did not gather enough momentum for it to become part of production designs in the way power management did.
Gene Amdahl's Thesis and the WISC Computer
You may be interested in reading Gene Amdahl's Ph.D. Thesis, University of Wisconsin, October 11, 1951. It is titled The Logical Design of an Intermediate Speed Digital Computer.2 The design described in the thesis was constructed at UW from 1952 to 1955. The floating-point unit was added in 1957. The computer—aptly named WISC, or Wisconsin Integrally Synchronized Computer—provided digital computing capabilities for both instructional and research use. WISC was retired in 1962, due to the cost of preventive maintenance and the recent arrival of a new IBM 1620.I discovered Gene's thesis in one of the subfloors of the main library at Wisconsin when I was looking for something else. I called Gene and started the process resulting in Gene's being able to meet with the Wisconsin CS Alumni group in Silicon Valley a few years later.
I later had a meeting with my Ph.D. advisor at the time and the Dead of the College of Engineering at Wisconsin about moving the one implementation of the WISC computer to the new main engineering building. That effort did not succeed, and the WISC computer is in the archive of the Computer History Museum where it cannot be seen. There is an old car in the engineering building where the WISC likely would have stood.
Collected Quotes
-
Here are some quotes I collected over the years:
- This came from Vern Bennett's eulogy during my grandmother, Ethel Eshom's funeral. She taught grade school for 37 years, before retiring in 1974.
- This Calvin Coolidge quote comes from Professor Charles Dyer's3 .plan file. When I was his teaching assistant I noticed it. President Coolidge was not an academic, but I agree with his ideas.
- I forgot to record where I found this one.
- This was quoted by multiple people at Jim Gray's rememberance ceremony at UC Berkeley on May 31, 2008, several months after his disappearance. I remember how cool it was when someone asked the audience who had been on Jim's boat, and about two-thirds of the about 500 (guessing—it could have been more) people there raised their hands. If someone knows how many people were there, send me an email and I'll put in the correct number.
- This is from Bjarne Stroustrup's book, The C++ Programming Language, 4ed.
She looked for something that each student did well, instead of looking for faults.—Dr. Vern Bennett, former Director of the Fargo, North Dakota Public School System.
Nothing in the world can take the place of persistence. Talent will not; nothing is more common than unsuccessful men with talent. Genius will not; un-rewarded genius is almost a proverb. Education will not; the world is full of educated derelicts. Persistence and determination alone are omnipotent.—Calvin Coolidge, 30th President of the United States of America.
Many of life's failures are people who did not realize how close they were to success when they gave up.—Thomas A. Edison, American Inventor.
A people hire A people, B people hire C people.—Jim Gray, database researcher and 1998 Turing Award winner.
You don't have to know every detail of C++ to write good programs.—Bjarne Stroustrup, inventor of C++.
Footnotes
1 The spelling of equals is as specified by the Unicode Consortium.2 Please follow the University of Wisconsin copyright guidelines for electronic materials when using this document. Also, there is a better copy of the thesis somewhere on the Internet. I did my copy with the Wisconsin Computer Sciences Department photocopier using a faculty member's borrowed (with permission) access code. The other one looks much better.
3 I found out about the September 11, 2001 attack on the World Trade Center when I walked into Chuck's class to be introduced as his TA. He told me what happened. I looked at the class and said, "This is a joke, right?" Chuck was nice enough to take care of the final project presentations for me, and Jim Smith was good enough to ensure my 899 Virtual Machines course partner was not penalized because I was unvailable when I had to return to North Dakota to bury my grandmother who raised me along with her daughter, my mother, who passed away about two years earlier.
