"Polite" wireless protocols:
privacy/security consequences
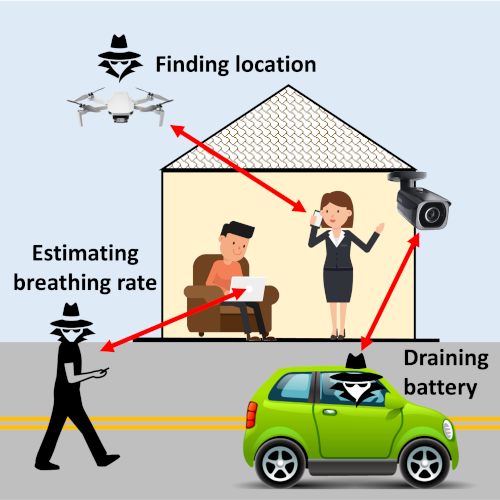 We found a loophole in the IEEE 802.11 standard (Wi-Fi) in which Wi-Fi devices respond to contact attempts from any device within range, even if the network is password protected. This loophole enables many security and privacy attacks.
We use this loophole to design Wi-Peep, a non-cooperative Wi-Fi localization attack, that can be used to locate Wi-Fi devices without any hardware or software modifications on the target devices. Wi-Peep uses a novel time-of-flight measurement scheme to locate target devices. Wi-Peep can be implemented on a lightweight drone, making it possible to locate Wi-Fi devices across multiple floors of a building to meter-level accuracy.
In another study, we have shown that an attacker can utilize the polite Wi-Fi loophole to estimate the breathing rate of a person from outside the building or from another building.
Recently, we have found that the "polite Wi-Fi" loophole is not limited to Wi-Fi, and other wireless protocols may suffer from the same issue. Specifically, we show that a similar problem exists in the popular Z-Wave standard that is used in many IoT applications such as Amazon Ring home security systems.
We found a loophole in the IEEE 802.11 standard (Wi-Fi) in which Wi-Fi devices respond to contact attempts from any device within range, even if the network is password protected. This loophole enables many security and privacy attacks.
We use this loophole to design Wi-Peep, a non-cooperative Wi-Fi localization attack, that can be used to locate Wi-Fi devices without any hardware or software modifications on the target devices. Wi-Peep uses a novel time-of-flight measurement scheme to locate target devices. Wi-Peep can be implemented on a lightweight drone, making it possible to locate Wi-Fi devices across multiple floors of a building to meter-level accuracy.
In another study, we have shown that an attacker can utilize the polite Wi-Fi loophole to estimate the breathing rate of a person from outside the building or from another building.
Recently, we have found that the "polite Wi-Fi" loophole is not limited to Wi-Fi, and other wireless protocols may suffer from the same issue. Specifically, we show that a similar problem exists in the popular Z-Wave standard that is used in many IoT applications such as Amazon Ring home security systems.