Mazharul Islam (মাজহারুল ইসলাম)

Recent News
| [May 24] I returned to Visa research this summer to address security and privacy issues of large language models. |
| [April 24] Our paper led by Majed got accepted to IEEE-Euro S&P! |
| [Feb 24] I passed my PhD proposal exam. I am a PhD candidate now! |
| [Jan 24] My work Compact got accepted to PETs 2024. |
| [Sep 23] Excited to participate and be awarded student travel grant from saTML. Thanks sponsors and organizers! |
| [Sep 23] Awarded student research grants from UW-Madison. | [May 23] My last summer's internship work at Visa Research "Compact" is on ArXiv. Feedbacks and comments are welcome. |
| [Aug 23] Presented our work “Araña" at USENIX Security 23. Here is a TL;DR tweet I made about the paper. | [Jul 23] Got student travel grant from USENIX Security 23. Thanks to USENIX organizers and sponsors! | [May 23] I returned to Visa Research this summer to work on account recovery problem in passwordless user authentication! |
About
I am a Ph.D. candidate (dissertator) in computer science at the University of Wisconsin——Madison, and my research area is in security and privacy. I am advised by Prof. Rahul Chatterjee, and I frequently collaborate with Prof. Thomas Ristenpart (from Cornell Tech) and Visa Research where I spent the last three summers as a staff research scientist intern.
I completed my M.Sc. in computer science also from University of Wisconsin-Madison in 2022, and before that completed my B.Sc. in computer science and engineering from Bangladesh University of Engineering and Technology (BUET) in 2017. My resume is available here.Research summary
I develop privacy preserving secure systems by designing novel privacy enhancing, machine learning techniques, and analyzing complex attacks on large-scale datasets.
My PhD thesis in particular focuses on solving security and privacy problems of online user authentication. Additionally, over the last seven years, I have been conducting research in diverse areas, as such before starting my PhD, I used to do research in the areas of computational biology, software security, and lightweight cryptography for edge devices.
Feel free to click on my ongoing and prior research projects below to know details.
User authenticationPublications: USENIX Security '22a, '22b, '23, two under submission
My PhD thesis is in the area of modern user authentication where I investigate how to safeguard users' online accounts against advanced attacks——all while carefully striking a right balance amongst privacy, usability, security, and deployability related crucial issues of the underlying authentication protocol. I have worked on the two most widely used online user authentication protocols: password-based, and passwordless as detailed in the following.Password-based user authentication: Passwords are the most popular, widely used, and convenient form of online user authentication. Unfortunately password based user authentication are prone to be vulnerable against advanced attacks. My work focuses on stopping attackers from launching password guessing attacks, and detecting malicious logins even against advanced attackers.
Passwordless user authentication: We have been observing a major industry led force in transitioning towards passwordless user authentication via passkeys. My ongoing work focuses on solving security problems of passkeys and FIDO2-based user authentication alike.Publications: PETs 2024, one ongoing work
I have also being working at the intersection of machine learning and cryptography to address the problem of secure training, and private inference. My recent work "compact" have addressed how to make complex activation functions used in machine learning secure multi-party computation (MPC) friendly. Currently I working on addressing securiy and privacy issues of autoregssive large language moels using cryptographic techniques.
Publications: BMC Genomics 2020, Bioinformatics journal 2022
Before starting my PhD, I used to work in the area of computation biology. I developed a dynamic programming based approach to estimate statistically consistent species tree from gene trees via maximizing the triplet consistency score. My another work involved developing a probabilistic method for filling genomic sequence gaps for short sequence reads.
My Master's thesis in BUET was related to security. It focused on developing lightweight cryptography for edge devices (published in MobiQuitous 2019)
Selected Projects
Feel free to click on the ``project summary button''' for more details
Compromising users account is perhaps the most lucrative attack vectors simply because it presents an entry point for attackers to undermine the security of an otherwise secure system, and cause subsequent harm to users.
This project is the result of four year long effors of researchers from University of Wisconsin-Madison, and Cornell University to discover and characterize attack campaigns to collect authentication logs and then discover new guessing attacks from the collected logs. To do this we first deploy and instrument a measurement framework to collect users authentication logs called "Gossamer". Then develop a filter, cluster, and analysis (FCA) pipeline called "Araña" to discover high and low volume attack campaigns from the authentication logs.
Existing breach alerting services from Google, Apple, Microsoft only check if the exact password is leaked, and therefore do not mitigate credential tweaking attacks
MIGP (Might I Get Pwned) is a next-generation password breach altering service to prevent users from picking passwords that are very similar to their prior leaked passwords. By doing do MIGP protects users from credential tweaking attacks where attacker attempts to compromise a user account with variants of a user’s leaked passwords. Recent work has shown credential tweaking attacks can compromise accounts quite effectively even when the credential stuffing countermeasures are in place.
Synced passkeys are a user-friendly solution for account recovery where passkey management services (PMS) from Apple, Google, Microsoft back up users’ FIDO2 private sign- ing keys to their cloud storage. This solution, however, ex- poses passkeys to the potential risk of PMS cloud storage compromise. Unfortunately, existing designs are unable to eliminate such a risk without reintroducing account recovery issues, leaving resulting abuse of leaked passkey difficult to detect.
In this work, we propose a new detection framework, CASPER, which enables websites to detect unauthorized lo- gin attempts by making passkeys stolen from PMS identifiable. Our analysis shows that CASPER provides compelling detection effectiveness, even against attackers who may strategically optimize their attacks to evade CASPER’s detection by leveraging useful information obtained from data breaches that many web services experience today. We also show how to incorporate CASPER seamlessly into the existing passkey backup, synchronization, and authentication processes while introducing only minimal impact on user experience, negli gible performance overhead, and minimum deployment and storage complexity for the participating parties

Spring security is tremendously popular among practitioners for its ease of use to secure enterprise applications. In this paper, we study the application framework misconfiguration vulnerabilities in the light of Spring security, which is relatively understudied in the existing literature.
Towards that goal, we identify 6 types of security anti-patterns and 4 insecure vulnerable defaults by conducting a measurement-based approach on 28 Spring applications. Our analysis shows that security risks associated with the identified security anti-patterns and insecure defaults can leave the enterprise application vulnerable to a wide range of high-risk attacks. To prevent these high-risk attacks, we also provide recommendations for practitioners. Consequently, our study has contributed one update to the official Spring security documentation while other security issues identified in this study are being considered for future major releases by Spring security community.
Secure multi-party computation (MPC) techniques can be used to
provide data privacy when users query deep neural network (DNN)
models hosted on a public cloud. State-of-the-art MPC techniques
can be directly leveraged for DNN models that use simple activation
functions such as ReLU. However, these techniques are ineffective
and/or inefficient for the complex and highly non-linear activation
functions used in cutting-edge DNN models.
We present Compact, which produces piece-wise polynomial
approximations of complex activation functions that can be used
with state-of-the-art MPC techniques. Compact neither requires
nor imposes any restriction on model training and achieves near identical model accuracy. We design Compact with input density
awareness and use an application specific simulated annealing type
optimization to generate computationally efficient approximations
of complex activation functions. We extensively evaluate Compact
on four different machine-learning tasks with DNN architectures
that use popular complex activation functions SiLU, GeLU, and
Mish. Our experimental results show that Compact incurs negligible accuracy loss while being 2×—5× faster than state-of-the-art
approaches for DNN models with large number of hidden layers.
Our work accelerates easy adoption of MPC techniques to provide
user data privacy even when the queried DNN models consist of a
number of hidden layers and complex activation functions.
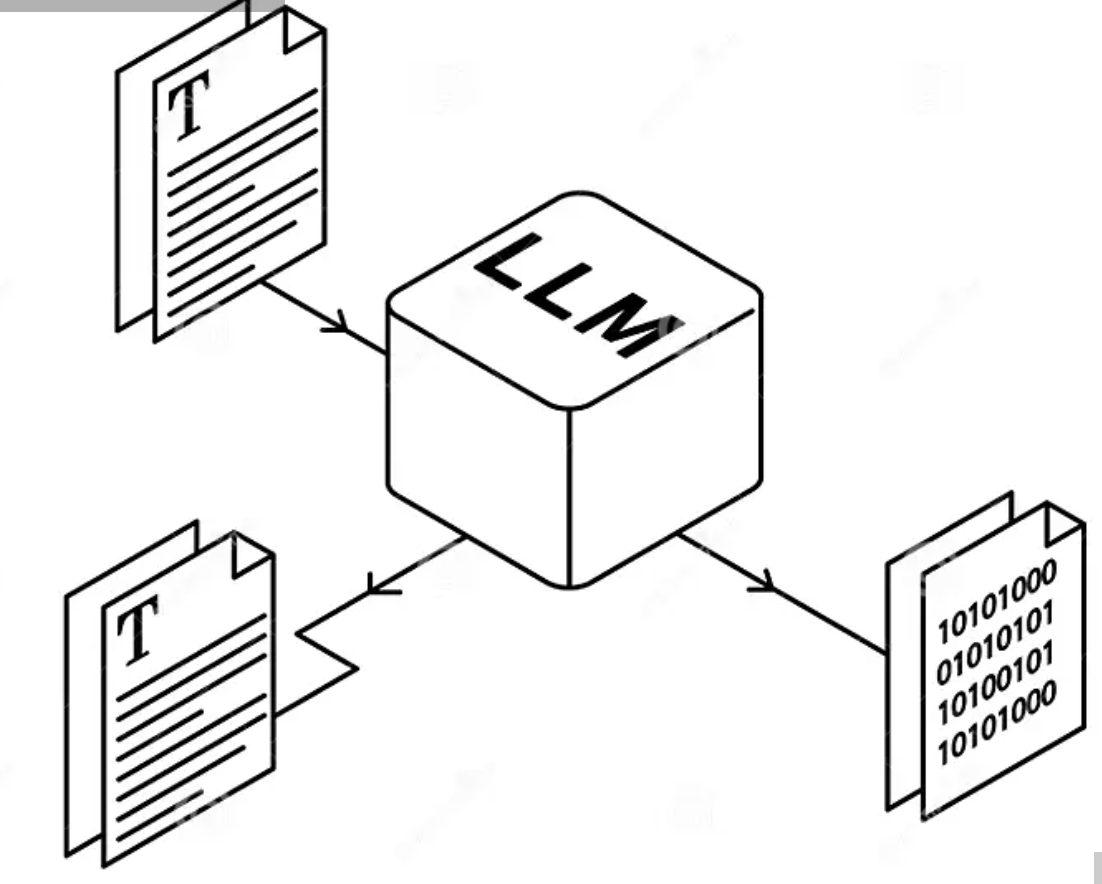
To solve the secure problem for LLMs, in this project, I am working on developing
- a new memory and communication efficient approach to securely evaluate non- linear functions used in LLMs
- a new secure matrix-matrix multiplication protocol

This is a firewall manager from scratch on top of a Linux program named iptables. I use React as frontend and Django as backend. The application was designed to help the network administrators to navigate and manage firewall rules with ease (similar to Cisco firewall manager).