1.5.1 What is SSH?
SSH (Secure Shell) is a program to log into another computer over a network, to execute commands on a remote computer, and to move files from one computer to another, in a secure manner.
[ Back to Top ]
1.5.2 Why use SSH?
Regular telnet connections transmit your password over the net in "plaintext" -- your password is not encrypted or protected in any way. It is possible for others to eavesdrop on the network and capture your username and password. With your username and password, they can then easily use your account, reading or changing your files, electronic mail, etc.
With SSH, your password never is transmitted without strong encryption.
Similar functionality is available with Kerberos, however it is more difficult to install and configure on private computers. Kerberos has been installed on all CSL workstations.
[ Back to Top ]
1.5.3 Can I use ssh on CSL Workstations?
SSH has been installed on CSL Unix workstations in /s/std/bin/ssh. When you wish to connect to a remote computer that supports ssh, type ssh remote-host where remote-host is the hostname of the other computer.
SecureCRT (ssh) is not installed on CSL Windows NT workstations at this
time. You can continue to use Kerberos Telnet for secure
connections from CSL Windows NT workstations to CSL Unix Workstations.
At the DOS prompt type ktel -x remote-host
where remote-host is the hostname of the other computer (Unix only).
[ Back to Top ]
1.5.4 Can I use ssh from home?
SSH can easily be configured for use from a home computer. Please read the instructions given in HOW-TO use SSH to establish a remote connection and transfer files
[ Back to Top ]
1.5.5 Can I securely transfer files to and from CS Department computers?
To securely transfer files over the network, you must use SSH port forwarding to establish a secure FTP session.
See Also:
- Setting up port forwarding on Unix
- Establishing a secure session (SSH) using secureCRT on my home Windows computer
[ Back to Top ]
1.5.6 Can I use SSH to read my POP mail?
POP mail can be read remotely and securely, by using SSH and port forwarding.
See Also:
- Reading POP mail from a home Unix workstation using SSH
- Reading POP mail from my home Windows workstation using SSH
[ Back to Top ]
1.5.7 Why doesn't SSH RSA Authentication work?
RSA Authentication is method for SSH to automatically authenticate the client, without the user typing a password.
RSA authentication does not work with CSL computers because it is necessary to authenticate to the AFS filesystem. The login process handles AFS authentication, using the password you provide. Without a password, it is not possible to authenticate to AFS.
See Also:
[ Back to Top ]
1.5.8 Security Considerations with SSH
Note: The security issues in this section apply equally to any SSH program. This answer is mostly from the SecureCRT documenation, modified for the specific case of the Computer Sciences Department.
There are important network factors in understanding SSH Security, especially when using Port Forwarding.
It is important to understand that the client data is only encrypted between the computer that is running SSH (local or client computer) and the SSH server (remote computer) that SSH is connected to. Any data moving from the SSH server across the network to another server is not encrypted. Three configurations are presented below to illustrate different computer/network configurations and their effect on security. Your evaluation of the connection between Servers A and B is the critical factor in deciding whether the aggregate security meets your needs.
Configuration 1
SecureCRT (SSH) forwards the FTP connection to a remote ftp server which is a different computer than the SSH server.
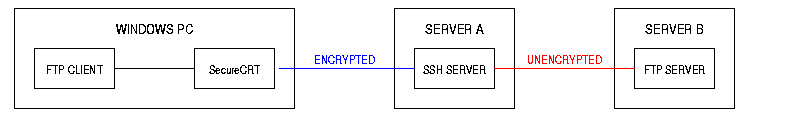
- Between the Windows PC and Server A the data is encrypted.
- Between Server A and Server B the data is not encrypted.
- Since the SSH server and FTP server are on different computers your data on this connection can be viewed by others.
In Configuration 1, the connection between Servers A and B could be:
- on the Internet - an unsecure network.
- on an internal LAN - a network which may or may not deliver a satisfactory level of security.
Configuration 2
SecureCRT (SSH) forwards the FTP connection to an FTP server which is running on the same computer as the SSH server.
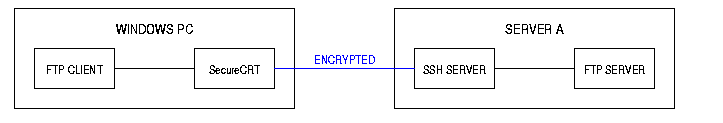
- Between the Windows PC and Server A the data is encrypted.
- Since there is no network traffic between the SSH server and FTP server, security is increased over Configuration 1.
Configuration 3
A SecureCRT (SSH) connection is made between a Windows PC and a Unix server. A telnet session is then made from the Unix server to another site.
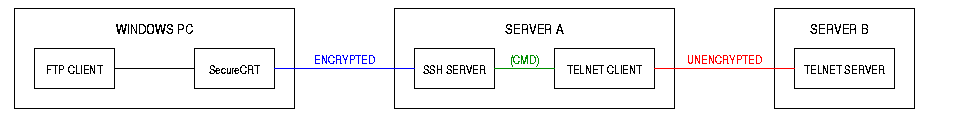
- Between the Windows PC and Server A the data is encrypted.
- Between Server A and Server B the data is not encrypted.
- Your data on the connection from Server A to Server B can be viewed by others.
- This is a variation on Configuration 1
[ Back to Top ]